As cyber threats have increased in recent years, simple reliance on password protection is insufficient to keep your data and resources safe. Multi-factor authentication is required for off-campus access to many JHU services, including access to the campus network via the VPN. Most of us are familiar with the Microsoft Authenticator on our mobile devices and use it either in One Time Password (enter code from the authenticator) or Push to Approve mode.
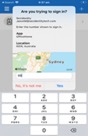
f you have “Push to Approve” enabled, this will be going away, and will be replaced with “Number Matching.” When you login to a protected application you will be presented with a 2-digit number and will receive a request to approve on your designated authentication device. Enter the number and press “Yes” to approve the connection. The number matching service will provide contextual information, including the application being accessed and a map location from which the sign-in attempt originated.
Please note that number matching is not yet available on smartwatches (e.g. Apple Watch), but Microsoft hopes to have this enabled in future. Those who use the OTP code in their authenticator, or use MFA via SMS text or phone call, will see no change. If you would like to switch to number matching from your current MFA method you can login to myit.jh.edu, select the “myPolicies” tile and select Enable MFA Number Match and Authentication Context.